 ChatGPT
ChatGPT
 Grok
Grok
 Perplexity AI
Perplexity AI
4 min read | By Postpublisher P | 24 January 2024 | Software Development
Internet connectivity has taken the world of the software industry to another level. It is almost impossible to imagine anything not surrounded by tech. The tech world is all about data exchange which should happen consistently to ensure smooth operations.
On the other hand, it is terrifying to even imagine what will happen if that data gets hacked or corrupted. This is why software testing companies extensively emphasise on VAPT Testing to ensure complete security for your software product.
In this blog, we will learn why VAPT testing is important to understand how its absence can cause you to pay a hefty price. And most importantly, we will discuss the checklist you must keep in mind to conduct VAPT testing precisely. Let’s start.
VAPT is a security testing process that helps businesses address and identify the security vulnerabilities in the system including applications, networks, information structure, and the overall infrastructure. It is mainly combined with two major testing approaches- Vulnerability Testing and Penetration Testing.
● Identifying misconfigurations and weaknesses in the hardware, software, and other network components.
● Conduct a risk assessment to prioritize vulnerabilities based on the intensity of the impact.
● Testing the security controls such as access controls, detection systems, and firewalls, to assess their effectiveness.
● Making attempts to exploit the identified vulnerabilities to get unauthorised access.
● Attempt to exploit the detected vulnerabilities to get unauthorised access.
These are the following points to clearly understand why VAPT testing is important.
● Security Improvement- The task of security improvement requires continuous enhancements to adapt to the evolving security challenges and threats. Security
controls include access control, setting up encryption from unauthorized access, and implementing firewalls to control network traffic.
Furthermore, security improvement also includes developing security procedures and policies to implement safe security practices. It’s important to protect the sensitive information of the users, employees, and other organizational data. VAPT assists in finding the vulnerabilities leading to data breaches.
● Mitigating Risks- VAPT testing supports the testing team to expand their focus on their resources to address critical vulnerabilities. After the identification of risks, organizations should focus on advanced strategies such as risk transfer, risk avoidance, risk acceptance, and risk reduction.
Also, documenting the entire process for risk mitigation is equally essential. Thus, documentation plays a huge role in future reference, accountability, and compliance.
● Reputation Management- Establishing a positive public image is crucial for any organization to grow and achieve success. Thus, VAPT testing helps prevent any critical issues at the earliest so you can take essential steps beforehand and protect your company’s image.
Communicating security efforts demonstrates a commitment to protecting systems and data with VAPT testing. Having a strong reputation in the security field ultimately leads to increased customer loyalty, trust, and competitive advantage.
● Compliance and Regulations- Different regions and industries require businesses to follow specific compliance and security requirements. Thus, VAPT Testing enables organizations to meet these requirements and secure sensitive data.Regulations help protect consumers from practicing unfair business means. Thus, VAPT testing protects them by following the Consumer Protection Act of different countries for product marketing and safety.
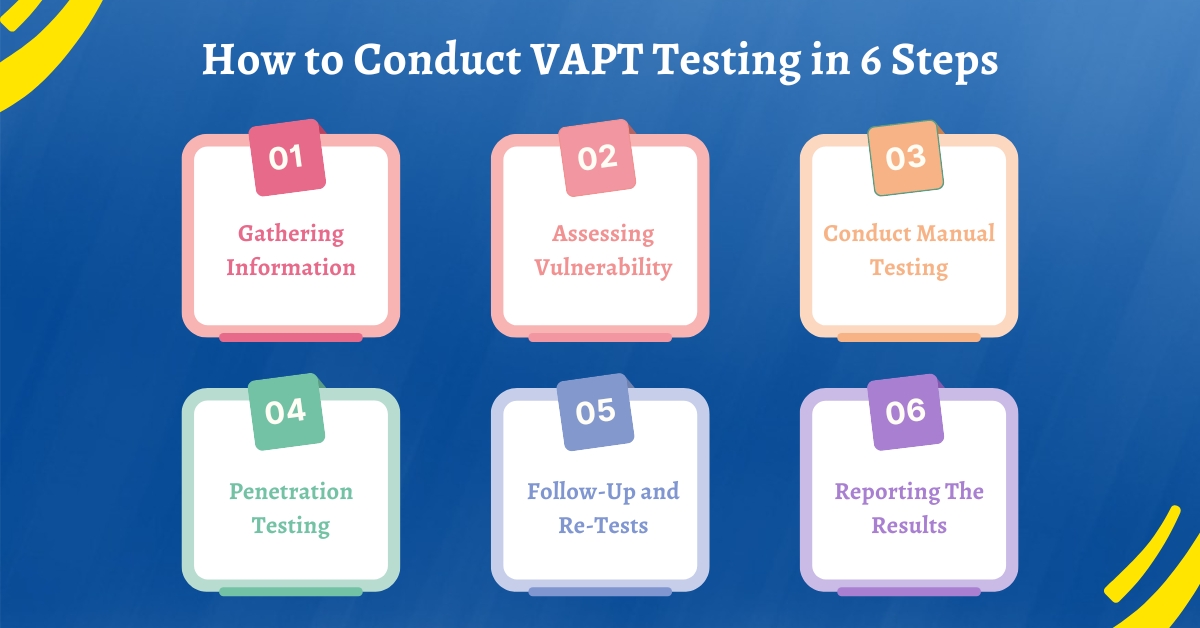
The first step in VAPT testing is to gather crucial information about the applications, target systems, etc. to begin the process. To begin, you need to define the scope of VAPT testing to set the boundaries for VAPT testing and ensure focused efforts,
Understand the business process and operational requirements. It enables testers to design the assessment process according to the main objectives and goals to find potential risks.
Along with that, gathering technical details which include information regarding web servers, operating systems, database servers, etc. This will allow the team to detect which section requires the most protection and categorize them for effective VAPT testing.
Scanning tools for vulnerability testing play a key role, especially in the initial stages of scanning the target systems. These tools detect the known weaknesses, vulnerabilities, operating systems, and weaknesses in the network.
Apart from that, vulnerability scanning also scans other hosts and devices connected to the network such as servers, routers, workstations, as well as IoT devices.
VAPT scanning in web applications highlights vulnerabilities such as authentication bypass, SQL injection, and cross-site scripting. Also, classify the intensity of the detected errors into medium, high, low risk, and critical.
Automated testing is no doubt the best testing method for repetitive tasks and finding common errors in VAPT testing. But, it doesn’t mean you should ignore manual testing completely.
Conducting manual testing requires significant skills to investigate applications, networks, systems, and other unconventional vulnerabilities that might get missed.
Ensure that your team emphasizes interactive sessions with fellow testers to understand the loopholes and the impact on the final results.
The task of penetration testing requires professionals to exploit the flaws, misconfigurations, and other significant security issues found during manual testing and vulnerability.
It is important to simulate real attacks on the system such as pretexting, baiting, and phishing, to evaluate its susceptibility and take important measures. However, it is important for the testers to follow ethical and legal boundaries to ensure that the testing is conducted under authorized parameters.
The main objective of this step is to determine the vulnerabilities found in the VAPT testing. It is essential to confirm that the security issues are mitigated before any major incident happens.
Also, regression testing ensures that the new changes have caused any new vulnerabilities. Documenting every step even in re-testing methods is also critical to validate that every step is taken carefully to resolve issues.
Businesses must implement necessary processes for regular security maintenance by adding security updates and patches. Hence, reinforcing continuous improvement is the key to reducing security breaches drastically.
After conducting all the necessary steps for VAPT testing, you need to process to report the results to the team. Summarize the outcomes and document the assessment to the development and testing team and other stakeholders.
The information should include information about the vulnerabilities identified during the process, potential impact, and the methods applied to verify them. Highlight the technical details of every vulnerability such as its impact, nature, and the difficulty level to resolve the issues.
Hence, effective reporting of results is important as it enables software testing companies in India to understand their current security conditions and make informed decisions to enhance their security.
In conclusion, VAPT testing provides you with a structured process that you must follow to ensure security in the current highly competitive scenario. The checklist for VAPT testing helps you develop a proactive approach to identify as well as mitigate security risks efficiently.
Also, the checklist highlights the importance of automated and manual testing to uncover complexities and simulate real attacks by adhering to ethical boundaries.
Therefore, by implementing a systematic approach, you can easily adapt to emerging trends without worrying about security vulnerabilities. Thus, follow the above VAPT testing checklist for best results and build a resilient software product.
Join over 150,000+ subscribers who get our best digital insights, strategies and tips delivered straight to their inbox.